The authors of SafeBrowse, a Chrome extension with more than 140,000 users, have embedded a JavaScript library in the extension's code that mines for the Monero cryptocurrency using users' computers and without getting their consent.
The additional code drives CPU usage through the roof, making users computers sluggish and hard to use.
SafeBrowse uses same technology tested by The Pirate Bay
The intrusive and highly damaging behavior was noticed almost immediately, as the extension's Web Store page has filled up in the past few hours with negative reviews decrying the surge in CPU resource usage.
Looking at the SafeBrowse extension's source code, anyone can easily spot that its authors embedded the Coinhive JavaScript Miner, an in-browser implementation of the CryptoNight mining algorithm used by CryptoNote-based currencies, such as Monero, Dashcoin, DarkNetCoin, and others.
At the time of writing, the Coinhive JavaScript Miner, as described on its website, only supports Monero mining.
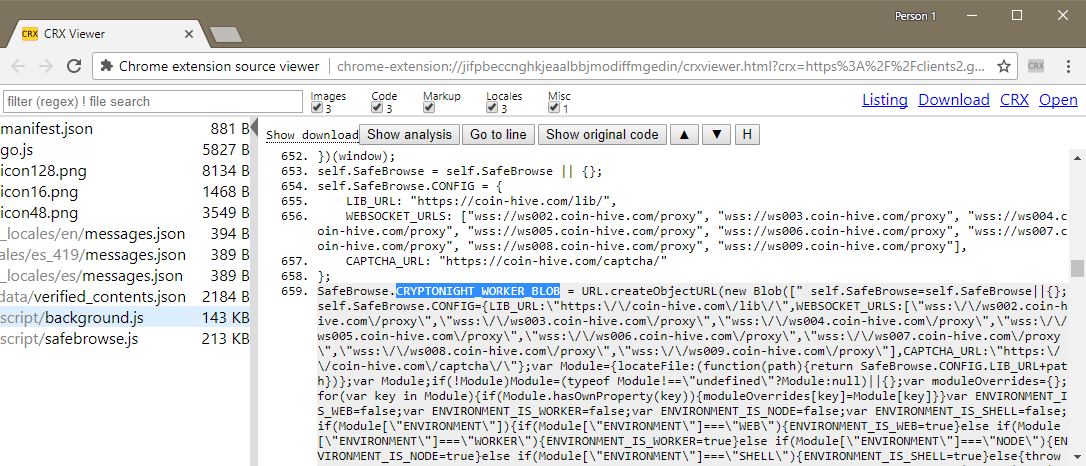
The above code starts a process that runs at all times in the browser's background and mines for Moner using the user's resources, but for the profits of the SafeBrowse authors.
Affected users include anyone who installed the SafeBrowse extension. The version featuring the Coinhive miner is 3.2.25. Chrome extensions use an auto-update system, so most SafeBrowse users will be updated to this version in the coming hours and days.
The addition of the Coinhive JavaScript Miner to SafeBrowse comes after The Pirate Bay experimented with the same technology as an alternative to showing ads on its site. Users who visited The Pirate Bay last Saturday did not see ads on the site, but the portal loaded a JavaScript file in their browsers that mined Monero for the torrent portal's owners.
SafeBrowse extension ruins your PC's performance
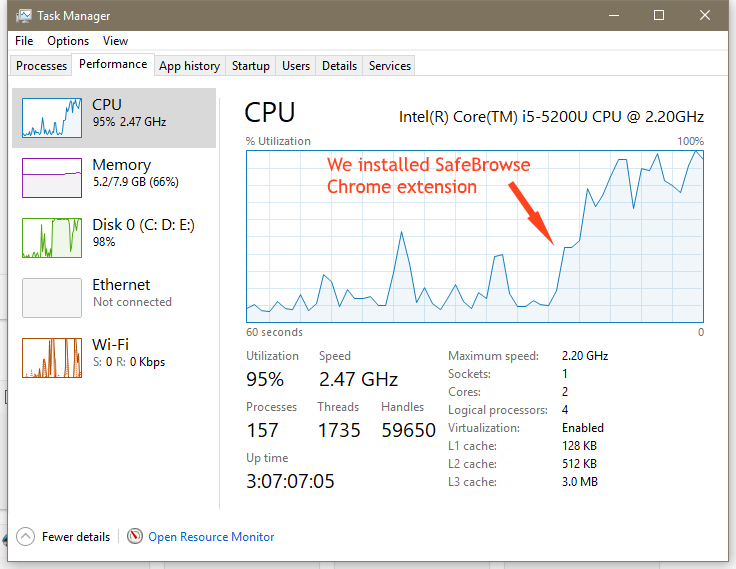
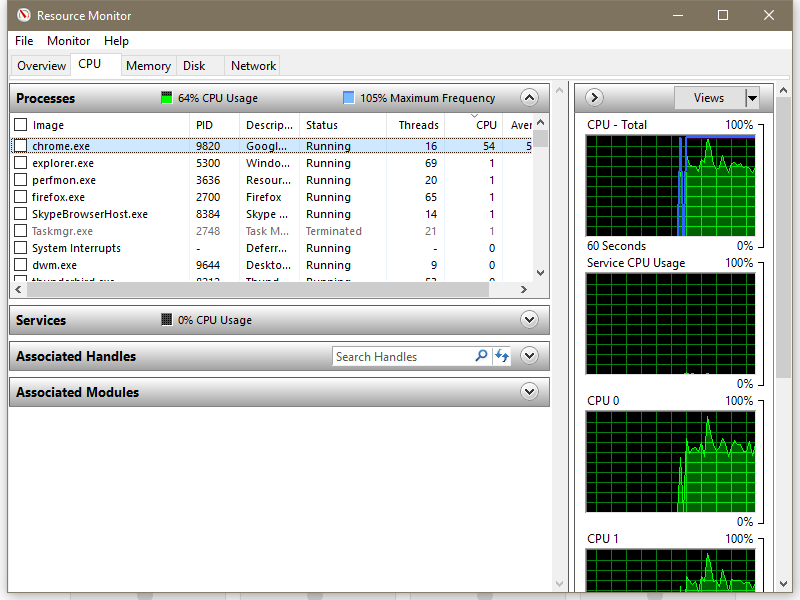
Bleeping Computer tested the extension, and the Monero mining operation is clearly visible in the Windows Task Manager and Resource Monitor applications, immediately driving up CPU resource usage shortly after installation.
|
|
|
The same spike in CPU usage can be seen in Chrome's built-in Task Manager, showing the extension's process taking up over 60% of CPU resources.
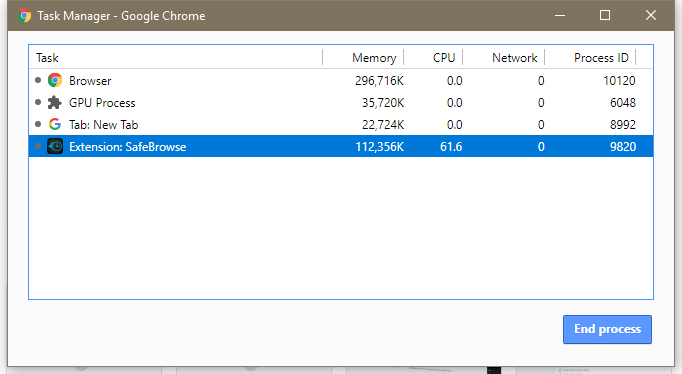
The impact on our test computer was felt immediately. Task Manager itself froze and entered a Not Responding state seconds after installing the extension. The computer became sluggish, and the SafeBrowse Chrome extension continued to mine Monero at all times when the Chrome browser was up and running.
It is no wonder that users reacted with vitriol on the extension's review section. A Reddit user is currently trying to convince other users to report SafeBrowse as malware to the Chrome Web Store admins [1, 2].
Not the first time doing something shady
At the time of writing, the SafeBrowse extension was still available for download through the Web Store, and neither its privacy policy or official website mention anything about the recent update and the addition of the Coinhive code.
This is not the first time the extension was caught doing something shady. Back in November 2015, researchers from Detectify Labs found that SafeBrowse, along with many popular Chrome extensions, where loading analytics code without consent in order to track users across the web.
Bleeping Computer has reached out for comment to SafeBrowse. We will update the article with any statement the authors wish to make.
UPDATE [September 19, 15:30 ET]: The SafeBrowse team has provided Bleeping Computer the following statement regarding the extension's recent Monero mining capabilities.
Unfortunately we have no knowledge, apparently has been a hack. I'm currently researching, I have already contacted the Google team. The extension has not received an update for months, so I do not know what it's all about.
While most users know how to remove a Chrome extensions, users who lack the technical skills and need help with removing the SafeBrowse extension can consult a guide we put together here.



Comments
Lawrence Abrams - 6 years ago
This is one way to take a widely used extension and destroy its popularity for a few $$$.
rhasce - 6 years ago
They are so stupid, as soon as people feel computer slow after installing their products people will leave them, and they are rats too.
Occasional - 6 years ago
Will have to look at the details more carefully - but it looks like another instance where Google's vetting process is inadequate.
There are pluses and minuses for users and developers with the Store/Play paradigm. While suitability, functionality and performance will be judged by the users; they should feel confident that what they load from that authorized source will not harm or steal from them (beyond the cost of a worthless product, if they decided to buy).
When the vendor-browser-store metric of success is based on quantity over quality, the incentive is to let everything through, and only look closer when someone (actually, a huge number of people), complains.
Occasional - 6 years ago
As at least part of the story is about funding choices (ads, reselling info or stealing system resources); just taking the opportunity to say what a pleasure it is to visit Bleeping Computer!
The ads are few, nonintrusive and relevant to the subject matter for most visitors.
If BC provides a download of something that has been compromised, they catch it quickly and provide notice as well as mitigation.
These are rare qualities, and getting rarer by the day.
jinmo123 - 6 years ago
(deleted)
Mehmet_Kececi - 6 years ago
There's been a significant detection. Thanks.
Warthog-Fan - 6 years ago
Just one more example of why I can't live without Bleeping Computer and their outstanding help and support.